We are living in a world where artificial intelligence (AI) is transforming eve....
Social Engineering and Risk from Cyber-Attacks

As the world is becoming increasingly digitalized, the risk of cyber-attacks is growing exponentially and hackers are continuously developing sophisticated methods to access sensitive information and confidential data. One of the tactics hackers use to manipulate people into revealing their sensitive information is social engineering.
What Is Social Engineering?
Social engineering is a cyber-attack method used to trick people into performing certain actions which comprise security. It is a type of psychological manipulation that exploits human vulnerabilities, such as trust, fear, curiosity, and greed.
The most common social engineering techniques are:
- Phishing attacks - These attacks happen when hackers use fake emails and impersonate someone trustworthy to trick users into giving them confidential information, such as login credentials or personal information.
- Smishing and vishing - These are two similar types of social engineering attacks. Smishing is a type of attack where the attacker uses text messages or SMS to lure someone into clicking a link or responding to the message. Vishing, on the other hand, is a type of attack where the attacker calls the victim and tries to trick them into providing sensitive information over the phone.
- Baiting - It is a type of social engineering attack where the attacker offers something tempting, such as a free gift or a quick fix, to trick the victim into doing a specific action, such as providing sensitive information or downloading malware.
- Tailgating - This is a type of physical security attack where an unauthorized person sneaks into a secure area by following someone else who is allowed to be there.
- Business Email Compromise (BEC) - By using this method, attackers gain access to an organization's email system and trick workers into disclosing sensitive information or transferring funds. They might pretend to be someone important or use tricks to make the employees do what they want.
- Quid Pro Quo - It is a type of social engineering attack where the attackers offer something, like a prize, in exchange for information or access. The attacker may pose as a technical support representative, a salesperson, or a researcher, and offer the victim a reward or benefit in exchange for performing an action or providing information.
Risks Posed by Social Engineering Attacks
Social engineering attacks pose serious risks to individuals and organizations. These attacks use deception and manipulation to exploit human behavior and can result in a variety of negative consequences, including:
- Financial loss
- Data breaches and loss of sensitive information
- Reputation damage
- Legal and regulatory consequences
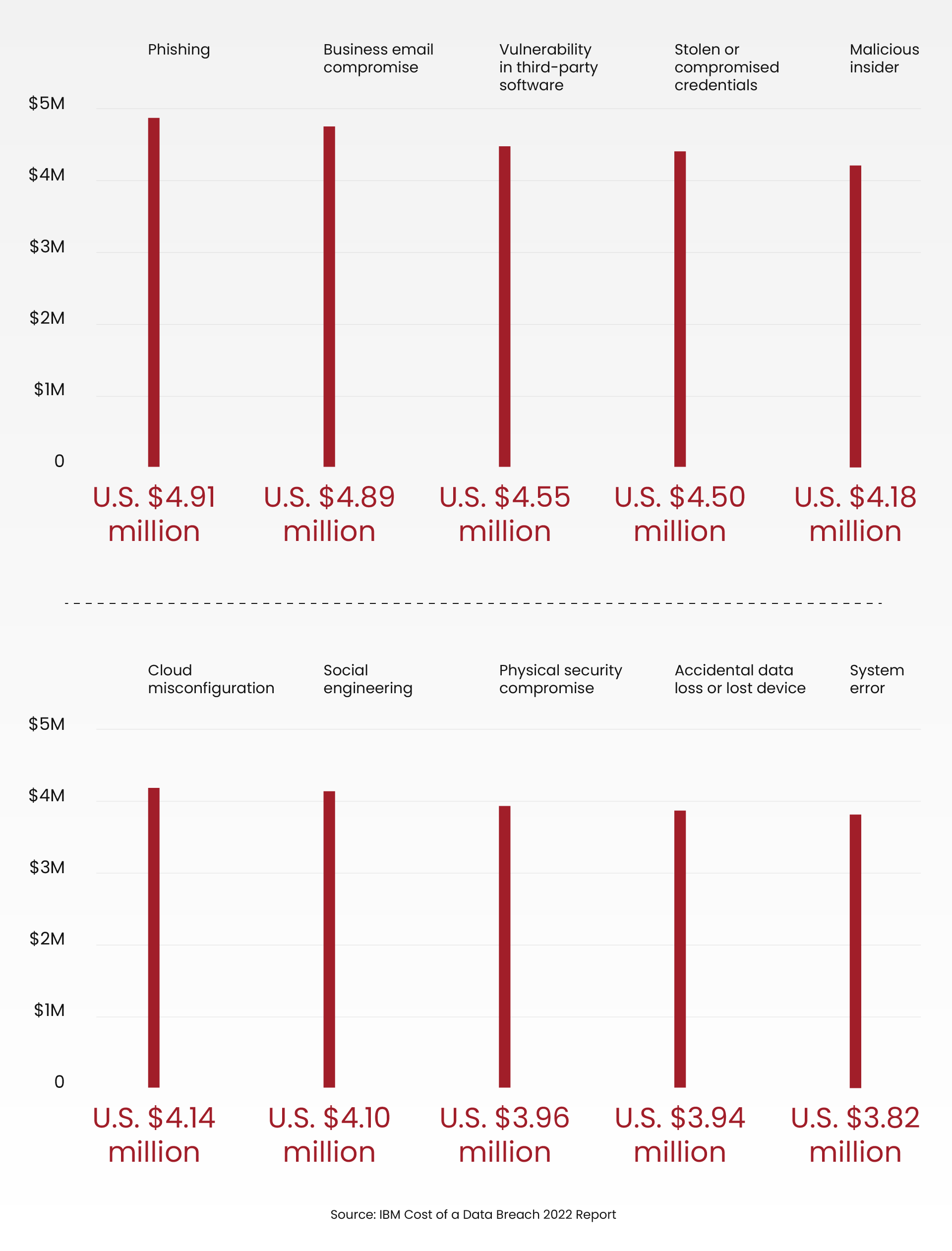
IBM reported that data breaches resulted in the loss of numerous millions of dollars, with the average cost of a data breach in the United States reaching $9.44 million. Each cyber-attack method incurred costs millions of dollars, as illustrated in the infographic below.
Prevention and Mitigation Strategies
Individuals and organizations are now facing higher risks from social engineering attacks due to the advanced nature and increased frequency of such attacks. Nonetheless, there are effective methods that can be employed to prevent and mitigate these risks.
A very good method to prevent social engineering attacks is educating and training employees to identify and avoid them. They should know how these cyber-attacks work, what signs to look for, and what steps they can take. These are crucial factors in preventing such attacks. That means every employee must know how to spot unusual emails or phone calls, ensure the authenticity of communications with others, and avoid suspicious links or downloads.
Preventing social engineering attacks can also be achieved by implementing security measures including two-factor authentication, spam filters, and firewalls.
To ensure that security protocols remain effective against evolving social engineering attacks, regular testing and updating are crucial. Techniques such as simulated phishing attacks, and software/systems patching can be employed to evaluate employee awareness and response.
Social engineering attacks might still occur despite many preventative measures, so it is important to have incident response plans in place to mitigate damage and minimize the impact.
Strengthening Cybersecurity with ISO Standards
Being on the Internet means that the risk of cyber-attacks is always permanent, and as explained, social engineering works by manipulating normal human behavioral traits. Therefore, a good way to be protected and ready to handle such attacks (technical and non-technical) is to implement fundamental processes and controls based on ISO/IEC 27001 and ISO/IEC 27032.
ISO/IEC 27001 is a globally recognized standard for information security management. It provides a framework for organizations to establish, implement, maintain, and continuously improve their information security management system (ISMS).
The ISO/IEC 27001 standard offers a systematic method for managing information security risks and enhancing an organization's cybersecurity stance via the utilization of risk management techniques, comprehensive security controls, and a continuous improvement process.
ISO/IEC 27032 is an internationally known standard that focuses on the cybersecurity of networked systems. It provides guidelines for improving the security of communication networks and helps organizations establish effective cybersecurity practices to protect against cyber threats.
By adopting the ISO/IEC 27032 standard, an organization can improve its cybersecurity posture in multiple ways, including safeguarding the confidentiality and integrity of the organization's data, reinforcing its cybersecurity programs, detecting and monitoring potential cyber threats, and facilitating a prompt response in the event of a security incident.
About the Author
Vlerë Hyseni is the Digital Content Officer at PECB. She is in charge of doing research, creating, and developing digital content for a variety of industries. If you have any questions, please do not hesitate to contact her at: content@pecb.com.


